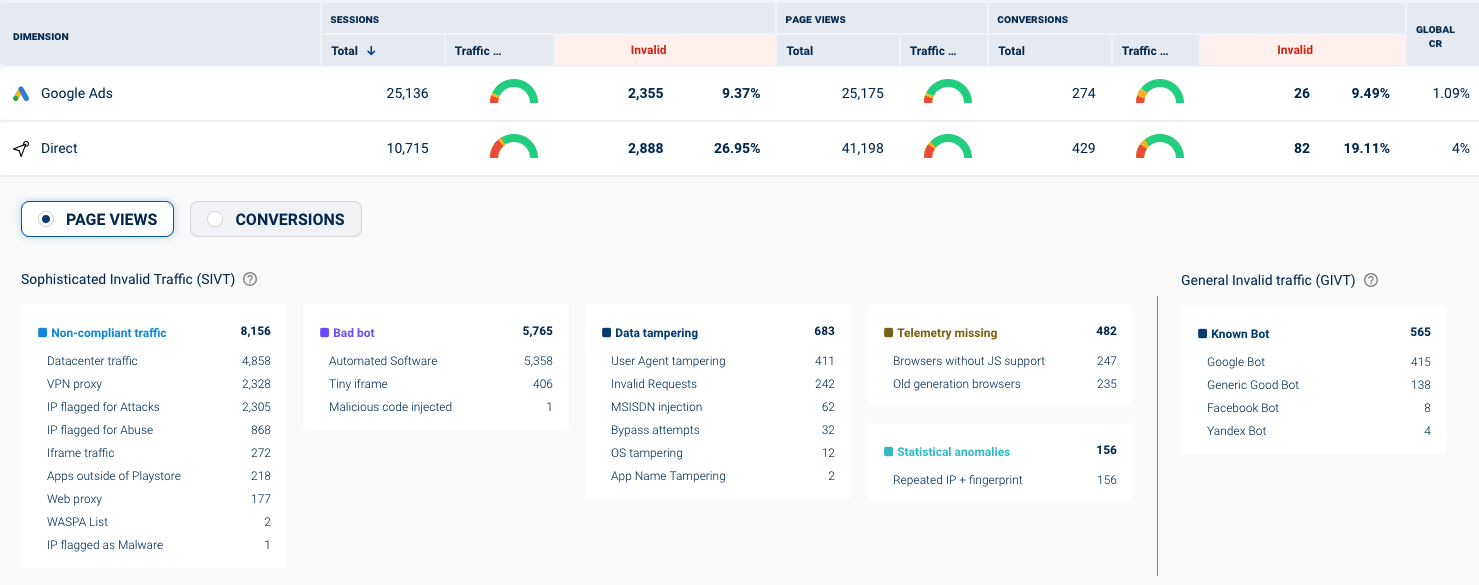
List of Opticks invalid traffic detections
Opticks classifies invalid traffic detections in a category (threat) and a detailed description (incidence). Each threat consist of a set of incidences, and each indicende belongs to a particular threat. For example, Bad bots is a threat, which includes detections such as Automated Software or Malicious code injected.
Opticks rules
All Opticks detections are based on collected browser and device telemetry, page context or network fingerprint. Detections are triggered by rules. Opticks has 3 different types of fraud detection rules:
Heuristic rules
- Used to detect bots and sophisticated fraud schemes
- Created from expert knowledge
- Machine learning (IA) is involved in this process
Statistical rules
- Applied only when conversions (leads) are integrated
- They identify statistical anomalies i.e. repeated users or high conversion rates
Listing rules
- 3rd party data sources
- Examples are IP detections, apps out of the Play Store or Adult keywords
Each rule has an internal score. When an analysis is completed, all the rules scores are added and the click is assigned a risk level (high, medium, low). These risk levels are translated into the product as invalid, suspicious or valid clicks. Sometimes a single rule is enough to determine it as invalid, i.e. any bot rule.
List of detections
Please be aware that each click can trigger either none, one or several of the following detections.
| Threat | Description | Related Incidences |
|---|---|---|
| Bad bots | A bot is an automated piece of software programmed to perform some task. Bad Bots refers to any automated software attempting to generate fraudulent income. In some cases, the Bad Bot is a malicious app on a user's device which attempts to generate profits by automating ad activity. This activity occurs without the user's knowledge and the malicious app often masks itself as a legitimate app. Malicious web sites can also perform similar fraud. Other common Bad Bots are automated pieces of software running on servers. Those can generate huge amounts of fake traffic in an attempt to generate CPC income, video views or fill in forms among other actions. |
|
| Non-compliant traffic | Traffic that, based on the use case, can be a harmful threat. For example, Iframe traffic can pose a risk in some cases, while in others can have its legitimate use. Same applies to traffic coming from users browsing with VPN's or from datacenter, which might affect geolocated products but be acceptable for others such as B2B companies. Another example is traffic coming from adult websites. |
|
| Data tampering | Opticks detects different types of tampered requests and abnormal behaviours, which are a clear indicator of fraud. The User Agent header identifies the device and software being used to visit the web page. In an attempt to hide their activity and access restricted content, fraudsters falsely identify the software they are using (i.e. the web browser). For example, a single bot running on a Linux server will pose as 30 different mobile browsers in order to access content meant for mobile devices while hiding the fact that all the traffic originates from the same device. Opticks can detect cases where the User Agent information is not consistent with the device features. HTTP header injection is a general class of web application security vulnerability which occurs when Hypertext Transfer Protocol (HTTP) headers are dynamically generated. Opticks, among other checks, looks for any headers containing MSISDN information, which is a clear indication of fraud. |
|
| Statistical anomalies | Besides the gathered telemetry, Opticks is able to use statistical analysis to improve the scoring of a visit. For example, Opticks allows to set custom conversion thresholds for identifying suspicious sources. |
|
| Telemetry missing | In some cases Opticks is not able to gather the telemetry needed to perform its analysis. The main reason of this behaviour is because the devices can’t execute JavaScript because it’s purposely disabled or are too old. |
|
| Incidence | Description |
|---|---|
| Automated software | Also known as bad bots. These are automated pieces of software running on servers, that can generate huge amounts of fake traffic in an attempt to generate CPC income, video views, fill in lead generation forms or subscribe users to premium services. |
| Malicious code injected | Opticks found some executed code known to be used by fraudsters to carry out malicious activities. |
| Hidden page | The user is not seeing the marketing asset or website, i.e. it is being loaded in the background or outside of screen viewport. |
| Time to conversion anomaly | Opticks found abnormal patterns in the time passing from the original click to the conversion. |
| Adult traffic | Opticks can detect traffic with adult (XXX) keywords found in the HTTP Headers. This can help protect mainstream products from receiving adult traffic. |
| Iframe traffic | An iframe (short for inline frame) is an HTML element that allows an external webpage to be embedded in an HTML document. If you are not very careful when allowing your pages to be shown within somebody else's HTML page, there is a considerable security risk. Opticks can detect traffic if it finds that your page is being shown inside an Iframe. |
| IP flagged as Malware IP flagged for Abuse | Opticks curates its own lists as well as subscribes to external lists of dangerous IP addresses. Dangerous IP addresses are those which have been known to generate spam, launch abuse and malware, or are known to be unreachable. These lists are updated on an hourly basis. |
| Datacenter traffic | A data center is a facility composed of networked computers. Fraudsters usually use data centers to run bot software on them or to anonymize their location. |
| VPN proxy | VPN's and other proxies hide the real location of an user. They are used for a number of reasons such as to hide the origin of the traffic, filter web content, to go around restrictions such as geolocation blocks and to provide anonymity when surfing the Internet. |
| Apps outside of Playstore | The application hasn't been installed from the official Google PlayStore. Google's PlayStore security and health checks are not being passed for this app. Be aware though that fraudsters are able to mis-represent the package name of the APK they use to generate fraudulent traffic and they usually use legit APK names to avoid being blocked. |
| Browser tampering | The user is tampering information about their browser. |
| User Agent tampering | The user is tampering their User Agent string, which may include device model, operative system and browser. |
| Invalid requests | Opticks could not decrypt the communications due to some error or malicious manipulation in the transmission of data. |
| MSISDN injection | HTTP header injection is a general class of web application security vulnerability which occurs when Hypertext Transfer Protocol (HTTP) headers are dynamically generated. Opticks specifically looks for any headers containing MSISDN information, which is a clear indication of fraud. |
| Bypass attempts | Attempts by fraudsters trying to bypass antifraud solutions like Opticks. |
| App Name tampering | The user is browsing from an app that is tampering or hiding its name, effectively hiding the traffic origin. This is an usual scenario with fake apps or apps distributing illegal content etc. |
| Repeated IP + fingerprint | A Frequency Capping can be configured in Opticks per combination of IP and proprietary fingerprint, detecting likely duplicated visits from the same devices. |
| Unusually high CR (low threshold) Unusually high CR (high threshold) | Traffic received in different Campaigns might have different particularities. This feature allows you to define a custom threshold percentage when detecting suspicious or dangerous conversion rate (CR) values per Campaign, allowing you to accommodate Campaign's configuration to the real characteristics of your traffic. You can set both a High and Low thresholds. |
| Unusually high subpublisher CR | Opticks found abnormal patterns in conversion rate for certain sub-publishers or sub-sources (that deviate a lot from the general values of the rest of subpubishers). |
| Old Generation Browsers | Browsers no longer compliant with current standards (usually 10+ years old). |
| Browsers without JS support | Block traffic without JavaScript support, for visits that can't run JavaScript. |
How are detections translated in the dashboard
Each of the above threats and incidences are taken into account by Opticks proprietary algorithms to generate a final risk score. Depending on the magnitude of said score, the click will be categorized as Low risk (legitimate traffic), Medium risk (suspicious traffic) or High risk (invalid traffic). You can see both threats, detections and risk level in the analytics dashboard section.